



Next: 5.6 Properties of Metapolicies
Up: 5.5 Metapolicy Examples
Previous: 5.5.5 Exception
Contents
5.5.6 Enforcement
The policy enforcing components need additional information affecting
the enforcement of all or a specific subset of policies. A few
examples are given in figure ![[*]](http://www.nm.informatik.uni-muenchen.de/common/icons/latex2html-97.1/cross_ref_motif.gif) .
.
Table 5.6:
Example enforcement metapolicies
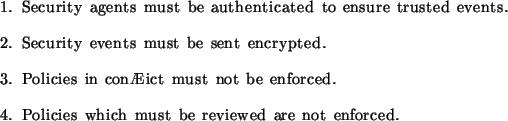 |
- In cases where the origin of events is crucial for the triggering of
management actions, extra constraints may be imposed on the sending
component. The first metapolicy ensures only the processing of
security events received from authenticated agents. Additionally, when
the content must not be made public, the agent is obliged by the
second metapolicy to send the events encrypted.
- The enforcement processes are given a rule how to handle policies
found being in conflict, e.g. through conflict metapolicies. Also
possible are guidelines for policies having a specific state
attribute. The last two examples show such metapolicies.
Copyright Munich Network Management Team
